
Design Basis Threat and The Active Shooter (Pt. 2)
Who exactly are we trying to protect ourselves against when we use the term “active shooter?”
For many, the answer to this question seems obvious—a “bad guy” killing people at random with a gun. However, this type of vague definition provides little guidance for developing an effective security design. A more useful definition considers:
- How many adversaries would possibly be involved in an attack?
- What is their level of skill?
- What types of weapons would they bear?
- What tools and methods of entry would they employ?
- Would the attacker(s) likely be an insider, outsider, or potentially either?
- Has the adversary employed any unique modus operandi in previous attacks?
Although many aspects of active shooter preparation are universal, these types of details have a major influence on the performance of our protective design and the benefit of system components (e.g., anti-personnel barriers, ballistic protection, etc.). Additionally, if our budget is limited, the answers to these questions can often guide us in prioritizing vulnerabilities of greatest concern.
As a security consultant, I’m frequently called on to assess facilities that have already invested in protective upgrades. In these situations, I frequently find examples of overlooked vulnerabilities, overconfidence in protective measures, or wasted expenditure. And these problems often stem from failing to define the attacker’s likely capabilities and methods as a driving factor in the original security design.
In professional approaches to security planning, this is the role of the Design Basis Threat (DBT) or Threat Definition. A DBT (or Threat Definition) provides a description of an adversary’s likely capabilities and tactics essential for determining the expected performance of security measures and identifying attack scenarios that should be addressed in security design.
Considerations for Developing a Design Basis Threat
Number of Attackers
The number of adversaries has a direct relationship to the potential effectiveness of our response force (i.e., Probability of Neutralization) and may influence the behavior of adversaries during attacks. One practical example is the likelihood of adversaries forcibly entering secured rooms to locate targets. Many documented incidents where adversaries forcibly entered locked rooms to seek targets involved more than one perpetrator.[1]
In the United States, the spectrum of active shooter adversaries has historically been quite diverse with most attacks committed by non-ideologically motivated perpetrators in alignment with Dr. Park Dietz’s definition of a pseudocommando.[2] The majority of these attacks are executed by a single attacker withstanding a handful of notable exceptions (e.g., 1998 Westside Middle School, 1999 Columbine High School, 2011 South Jamaica House Party, and 2012 Tulsa[3]). Historically, most terrorist-related active shooter attacks in the United States also involved only one perpetrator with exceptions including the 2015 San Bernardino and 2015 Curtis Culwell Center attacks.
Regional trends in adversary characteristics vary greatly in different parts of the world. In locations where terrorist attacks are the predominant concern, the number of perpetrators in attacks is often higher. In a study of 20 Marauding Terrorist Firearms Attacks (MTFA) conducted by the Critical Intervention Services in 2015, 1-2 perpetrators was most common in active shooter assaults in Europe with notable exceptions being events such as the 13 November Paris attacks.[4] In Africa, by contrast, terrorist groups such as Al-Shabaab frequently use teams of 4-9 attackers in assaults on civilian locations such as the Westgate Shopping Mall (2013), Garissa University (2015), and numerous hotels in Mogadishu.[5]
Relationship to the Facility/Organization
Is the adversary possibly an “insider” (e.g., current student, employee, etc.)? Or do the characteristics of our organization and environmental circumstances likely limit our concern to “outsider” adversaries? The answers to these questions often determine the relevance and priority of protective measures.
For instance, if the adversary is most likely an outsider, protective measures associated with perimeters, building facades, and entry controls are a high priority. By contrast, if the probable adversary is an insider, it is often wise to focus on indoor protective measures if the budget is a limiting concern.
In school settings, the probable type of adversary is largely influenced by the age of students. Withstanding a handful of plots, shooting events in primary schools have been executed by adult-aged outsiders (e.g., 2017 North Park Elementary School, 2012 Sandy Hook, 2006 West Nickel Mines, etc.) and a handful of expelled students (e.g., 2016 Townville Elementary School). In secondary schools, the spectrum of perpetrators is more diverse including both current and former students, and to a lesser degree, adult-aged outsiders.
In closed workplace settings, the majority of mass shootings are committed by current or former employees (e.g., 2020 Molson Coors, 2019 Henry Pratt Co., 2019 Virginia Beach Municipal Center, etc.). Although less common than employee-related shootings, there have also been cases of nonemployees (outsiders) targeting businesses for reasons of personal or ideological grievance such as the 2018 shooting at YouTube headquarters and the 2015 Charlie Hebdo attack.
In attacks against houses of worship and ethnic cultural centers, outsider adversaries motivated by ideology or reasons of personal grievance have been most common. Some recent examples include attacks at the Poway Synagogue (2018), Tree of Life Synagogue (2018), First Baptist Church (2017), Burnette Chapel Church of Christ (2017), Emanuel AME Church (2015), and Overland Park Jewish Center (2014).
Outsiders have also been the dominant category of adversary in attacks against public entertainment venues such as nightclubs, theaters, entertainment districts, and festivals. In many of these situations, the venue is targeted due to mass casualty potential or the characteristics of its patrons. Examples in recent years include attacks at the Nels Peppers Bar (2019), Gilroy Garlic Festival (2019), Borderline Bar and Grill (2018), Jacksonville Landing (2018), Route 91 Harvest Festival (2017), Reina nightclub (2017), and Pulse nightclub (2016). Although most attacks in entertainment facilities are premeditated, there have also been cases of disputes among patrons escalating into mass violence such as the 2017 shootings at the Power Ultra Lounge and Cameo nightclub.
In situations where terrorism is the primary concern, outsider adversaries should be the first priority. Although there have been attacks executed by radicalized employees (e.g., 2019 Naval Air Station Pensacola, 2015 Inland Regional Center, 2009 Fort Hood, etc.), the overwhelming majority of terrorist armed assaults are executed by outsiders.
Entry Tools and Methods
The delay time value of barriers (e.g., doors, locks, glazing, etc.) is directly related to the tools and methods adversaries may use to breach our barriers. Attacker tools and entry methods was one of the issues the CIS MTFA study team examined with the aim of creating a research-supported justification for defining threat capabilities.[6] Of the attacks assessed as part the study, in none of the events did attackers arrive equipped with tools (other than firearms) for the specific purpose of penetrating barriers. In case research conducted by CIS about other armed attacks against facilities over the past 20 years, the number of incidents where adversaries brought tools specifically for forced entry purposes was few. In the majority of attacks, forced entry was facilitated exclusively by blunt object impact (e.g., kicking, beating with rifle butt stock, etc.) and sometimes aided by bullet penetration or cutting with a bladed weapon.
For the purpose of designating or planning potential safe rooms, another issue worth considering is adversary effort and commitment to attack people located inside locked rooms. Joseph Smith and Daniel Renfroe describe their observations on this matter in an article on the World Building Design Guide web site: “Analysis of footage from actual active shooter events have shown that the shooter will likely not spend significant time trying to get through a particular door if it is locked or blocked. Rather they move to their next target. They know law enforcement is on its way and that time is limited. “[7] Separate case study research conducted by Critical Intervention Services also supports this perspective.
In a large percentage of attacks, adversaries focus solely on targets of easiest opportunity by using visually-obvious pathways and unlocked/unobstructed portals (e.g., doors, windows, etc) to facilitate indoor movement. This behavior may be due to perceived time pressure (“kill as many as possible before the police arrive”) or possibly diminished problem-solving ability resulting from activation of the Sympathetic Nervous System (SNS). In most documented attacks where adversaries committed effort to forcibly enter locked rooms, intervention by police or security forces was delayed and adversaries had exhausted all targets in accessible areas.
When developing a DBT for use in a region where the main threat concern is a particular terrorist group, research should focus on identifying any unique tactics or preferences for entry methods demonstrated in previous attacks. Al-Shabaab, for instance, has employed disguise and deceptive entry tactics for gaining access through the outer perimeter of several protected facilities in Somalia. If we were developing a DBT for Al-Shabaab, it would be wise to consider attack scenarios employing deception and disguise in addition to overt entry methods.
Weaponry
Weaponry influences the potential effectiveness of our response force, and caliber and type of ammunition determines the effectiveness of ballistic barriers in resisting bullet penetration.
According to FBI statistics, handguns were the most powerful firearm used in most attacks (59%) with rifles constituting 26% of incidents.[8] Although the FBI has not published statistics on weapon calibers used in active shooter attacks, most mass casualty attacks where rifles were employed in the United States involved 5.56mm weapons with examples including assaults at the Pulse Nightclub (2016), Inland Regional Center (2015), Sandy Hook Elementary School (2013), and Aurora Century 16 Theater (2012).
Outside the United States, 7.62x39mm weapons (AK-47) have been most common.
Likelihood of a Hostage/Siege Event
Although not directly related to adversary capabilities, another possible factor to consider is the likely duration of an event. If the adversary is a terrorist group with a specific preference for hostage-taking or if we are located in a region where there has often been delayed intervention by police/security forces, circumstances may justify a more advanced level of preparation.
In the 2015 CIS MTFA study, 35% of all attacks escalated into a siege by police/security forces upon arrival. In a number of these incidents, intervention was delayed due to early confusion about the event (“hostage situation” versus “armed massacre”). Some events resulted in a siege when arriving police or security forces were overwhelmed by the adversary’s firepower and withdrew pending the arrival of more assistance. In other events, police and security forces made committed entry but the size of facility and movement of the attackers inside the building delayed location and neutralization of the adversaries (e.g., 2019 Virginia Beach Municipal Center, 2013 Washington Navy Yard, 2015 Corinthia Hotel Tripoli, etc.).
Incidents documented in the CIS study that escalated into a siege had a duration ranging between 2h 24m and est. 96 hours, with a mean duration of 21h 44m. Although most events resulting in siege durations over 2 hours were in Africa or West Asia, recent incidents have occurred in Western countries with effective response times over 2 hours such as the 2016 Pulse Nightclub shooting (194 minutes from first call to 911) and Bataclan Theater (~156 minutes from first call to 112).
Developing a Design Basis Threat for Active Shooter Attacks
In the government community, many organizations promulgate official DBT statements to serve as a standardized reference throughout the organization. For instance, the Interagency Security Committee (ISC) in the United States produces a Design Basis Threat (DBT) document for use during risk assessments and security planning in Federal facilities. The ISC DBT includes several threat scenarios related to armed attack with narrative descriptions of the event, and adversary characteristics such as numbers of adversaries, weaponry, tactics, etc.
The US Department of Defense also provides similar guidance for DoD facilities in UFC 4-020-01 “DoD Security Engineering Facilities Planning Manual.”[9] In Table 3-27, DoD presents a generic DBT (Threat Parameters) including several categories of Aggressor Tactics and a system for defining progressive levels of threat. Each threat level is attributed a corresponding description of weaponry, toolset, and/or delivery method.
As a consultant, I am not an advocate of adopting generic DBTs unless required by official mandate. Instead, I prefer using a research-based approach which considers the specific characteristics of relevant adversaries, historical attack data, regional trends, and similar issues. This type of approach is often more laborious, but results in a custom DBT that is rational, justifiable, and specific to the threat situation.
When developing a custom DBT, I typically begin by collecting data about attacks against similar facilities in the region or attacks perpetrated by adversaries of relevance with focus on weaponry, number of attackers, and tactics. The following table illustrates how this type of data collection might be applied for a facility in Kenya where Al-Shabaab is the primary adversary of concern.
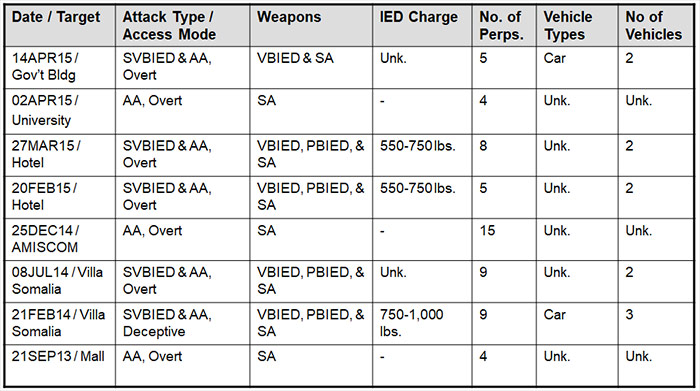
After data has been collected, a threat definition is then developed representing likely adversary capabilities and modus operandi. In a basic approach, the DBT is written to match any capabilities well established by trend or average. In a cautious or very cautious approach, the DBT matches or exceeds the highest level of capability as demonstrated in previous attacks.
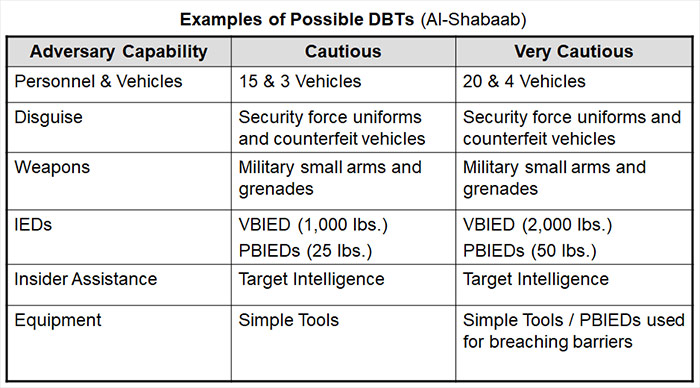
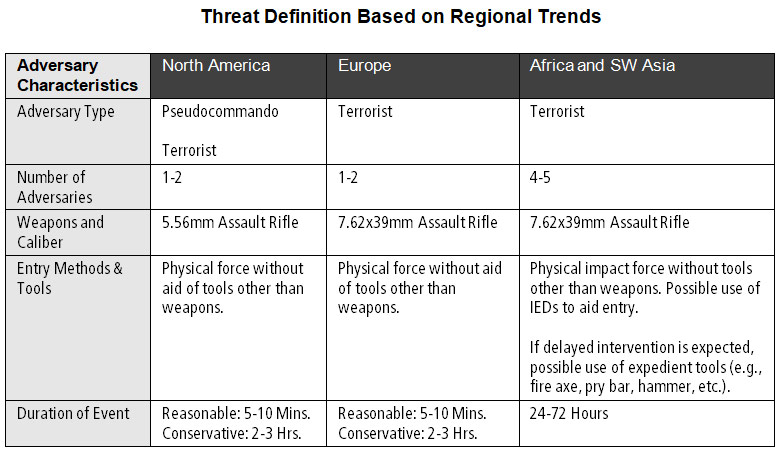
Even in situations where there are no unique adversary groups to serve as a model, this same type of research-supported approach can be applied for creating a non-specific, but justifiable DBT. Following are some examples of reasonable threat definitions based on historical attack data and well-established trends in different regions of the world.
[1] Examples including the 2015 Corinthia Hotel Tripoli attack and 2008 Taj Majal attack.
[2] Dietz, Park D. “Mass, Serial, and Sensational Homicides.” Bulletin of the New York Academy of Medicine. 62:49-91. 1986.
[3] Blair, J. Pete, and Schweit, Katherine W. A Study of Active Shooter Incidents, 2000 – 2013. Texas State University and Federal Bureau of Investigation, U.S. Department of Justice, Washington D.C. 2014. pp. 7. PDF. (The 2011 South Jamaica and 2012 Tulsa shootings are specifically noted as the only events involving more than one attacker in the FBI’s study of U.S. domestic active shooter attacks between 2000 and 2013.)
[4] Gundry, Craig S. “Analysis of 20 Marauding Terrorist Firearm Attacks.” Preparing for Active Shooter Events. ASIS Europe 2017, 30 Mar. 2017, Milan, Italy.
[5] Gundry, Craig S. “Threat Assessment Methodology and Development of Design Basis Threats.” Assessing Terrorism Related Risk Workshop. S2 Safety & Intelligence Institute, 25 Apr. 2017, Brussels, Belgium.
[6] Gundry, Craig S. “Analysis of 20 Marauding Terrorist Firearm Attacks.” Preparing for Active Shooter Events. ASIS Europe 2017, 30 Mar. 2017, Milan, Italy. (Presentation included results of an unpublished 2015 study by Critical Intervention Services.
[7] Smith, Joseph, and Daniel Renfroe. “Active Shooter: Is There a Role for Protective Design?” World Building Design Guide, National Institute of Building Sciences, 2 Aug. 2016, www.wbdg.org/resources/active-shooter-there-role-protective-design. Accessed 22 Sept. 2017.
[8] Blair, J. Pete, Martaindale, M. Hunter, and Nichols, Terry. “Active Shooter Events from 2002 to 2012.” FBI Law Enforcement Bulletin. Federal Bureau of Investigation, 1 July 2014, https://leb.fbi.gov/2014/january/active-shooter-events-from-2000-to-2012. Accessed 22 Sept. 2017.
[9] UFC 4-020-01, DoD Security Engineering Facilities Planning Manual. US Department of Defense, N.p.: 2008.

Craig Gundry
Copyright © 2020 by Craig S. Gundry, PSP, cATO
CIS consultants offer a range of services to assist organizations in managing risks of active shooter violence.
Contact us for more information.